The subject of IT security has been elevated to unprecedented levels.
Between phishing, ransomware and state-sponsored cyber-attacks, security breaches are now a daily occurrence. And the evolution of malicious technology never stops; attackers are more sophisticated now than ever and are looking to catch you, your MSP and your end customers off your guard. To stay ahead of the cybersecurity curve, MSPs need to evolve from a post-incident to pre-incident strategy.
In our recent webinar, Security, Services and Sales!, Liongard VP of Sales Shawn Sailer explains how MSPs can build a strong security foundation to stop breaches before they happen.
Almost every cybersecurity solution we’re familiar with today combats threats post-breach. They let you know about security issues only after the attacker has made it into your systems. Those solutions—anti-virus, intrusion detection, etc.—are just going to let you know the bad guys made it in; they’re not going to keep them from breaking in the front door. And firewalls are permeable. Attackers are going to go around them, under them and through them and your MSP has to be positioned well enough to defend your systems. Because it’s not a matter of if a breach will happen, but when.
“The reality is, you can’t stop everything,” says Shawn. “You can have the greatest anti-virus and firewalls, but as long as there is a human involved, there’s going to be a breach. You need to be able to predict the paths an attacker will take so you can minimize your exposure, and you need to have full visibility into all of the systems that you are responsible for covering for better control. But the key thing is, you can’t have a bunch of different configurations in your customer environments. You need to standardize to keep a handle on them and also to help you scale.”
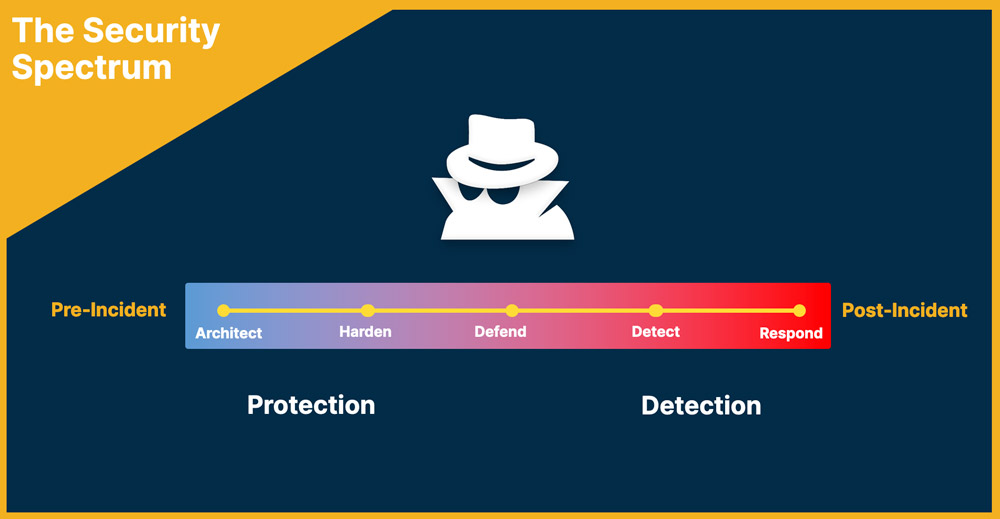
Now let’s put this into context. If you think about cybersecurity as a straight line, imagine that the middle of the line is when an attack happens. Most MSPs tend to have tools that address everything to the right, or after, the attack. This puts you into a position where you have to react, respond and recover, and that’s just not enough today. The challenge is to start thinking about security from the right of, or before, the attack. As an MSP, there are things you can do to keep bad actors from ever gaining access in the first place.
Streamline for Security (and Sanity!)
Today’s IT landscape is chaotic and complex and, if you’re like most MSPs, your security and other data are scattered throughout different apps and programs, each with its own portal and its own reporting. You typically have to look at each system customer by customer, making it almost impossible to manage efficiently. A lot of the time, MSPs try and tackle the problem with more techs, but this can negatively impact revenue. But the reality is, you have to have full visibility and reporting into these systems, and you have to know how they are configured so you can protect them.
You need to know when systems changes are made, and when you’re managing IT at scale, all the disparate systems can create a security headache, not to mention an exhausted engineering team. Let’s face it. The days of the traditional network perimeter and siloed security are gone. We know what works and what doesn’t, and what doesn’t work is doing manual discovery and documentation of all your systems. Your systems audits need to be frequent, comprehensive and scalable so that you’re prepared for attacks whenever they occur. What does work is automation and data unification that enable you to continuously detect potential risk exposures in your customer’s security posture.
“As an MSP, you have to provide a management plan that addresses the potential threats, both seen and unseen. It’s not what you know that will kill you, it’s what you don’t know or don’t see. That’s where data comes into the mix”
Data is King
When it comes to building a strong security foundation, data is king. Data is what will enable you to be proactive about monitoring systems and mitigating risk. The data will tell you if users have too many privileges, if customers have old, but still active, user accounts and other critical security information that is key to staying proactive. And for data gathering, consolidation, alerting and reporting, automation is essential.
You can use automation to track and monitor for:
- Drift of configurations
- Unexpected changes
- Activity on stale accounts
- Anomalous behavior
- Proper MFA implementation
This continuous monitoring enables you to remain alert to any changes and nimble enough to resolve them in a timely manner to prevent serious incidents from happening.
There are also some ancillary benefits associated with automated systems monitoring. This type of full data visibility allows you to combine systems data with your industry knowledge to create high-impact results for your customers. Insights from data help you close the door on vulnerabilities while opening the door to new opportunities. With the right data and automation, you can do things that enable great relationships with customers, like better reporting for billing and reconciliation, creating killer QBRs, simplifying onboarding and providing continuous systems assessments.
It Starts with the Right Tools
Constant and consistent monitoring of your customers’ systems will let you know the first sign of security trouble so that you can take proactive steps to mitigate damage and impact on the business. Liongard’s unified visibility platform and Actionable Alerts give you full visibility across your customer’s whole stack, all in one place, for systems monitoring that makes it easy to build a strong security foundation to standardize, secure and scale your MSP.
See what Liongard can do for you. Schedule your demo today.